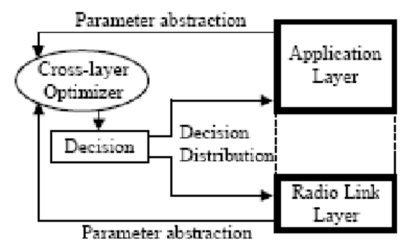
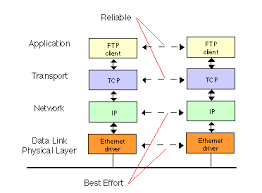
While a wireless network is more versatile than a wired one, it is also more vulnerable to attacks. This is due to the very nature of radio transmissions, which are made on the air.
On a wired network, an intruder would need to break into a machine of the network or to physically wiretap a cable. On a wireless network, an adversary is able to eavesdrop on all messages within the emission area, by operating in promiscuous mode and using a packet sniffer (and possibly a directional antenna). There is a wide range of tools available to detect, monitor and penetrate an IEEE 802.11 network, such as NetStumble, AiroPeek, Kismet, AirSnort, and Etherea.. Hence, by simply being within radio range, the intruder has access to the network and can easily intercept transmitted data without the sender even knowing (for instance, imagine a laptop computer in a vehicle parked on the street eavesdropping on the communications inside a nearby building). As the intruder is potentially invisible, it can also record, alter, and then retransmit packets as they are emitted by the sender, even pretending that packets come from a legitimate party.
Furthermore, due to the limitations of the medium, communications can easily be perturbed; the intruder can perform this attack by keeping the medium busy sending its own messages, or just by jamming communications with noise.
Attacks against the routing layer in MANETs
We now focus on attacks against the routing protocol in ad hoc networks. These attacks may have the aim of modifying the routing protocol so that traffic flows through a specific node controlled by the attacker. An attack may also aim at impeding the formation of the network, making legitimate nodes store incorrect routes, and more generally at perturbing the network topology.
Attacks at the routing level can be classified into two main categories: incorrect traffic generation and incorrect traffic relaying 6. Sometimes these coincide with node misbehaviors that are not due to malice, e.g. node malfunction, battery exhaustion, or radio interference.
Incorrect traffic generation
This category includes attacks which consist in sending false control messages: i.e. control messages sent on behalf of another node (identity spoofing), or control messages which contain incorrect or outdated routing information. The network may exhibit Byzantine behavior, i.e. conflicting information in different parts of the network. The consequences of this attack are degradation in network communications, unreachable nodes, and possible routing loops.
Cache poisoning
As an instance of incorrect traffic generation in a distance vector routing protocol, an attacker node can advertise a zero metric for all destinations, which will cause all the nodes around it to route packets toward the attacker node. Then, by dropping these packets , the attacker causes a large part of the communications exchanged in the network to be lost. In a link state protocol, the attacker can falsely declare that it has links with distant nodes. This causes incorrect routes to be stored in the routing table of legitimate nodes, also known as cache poisoning.
Message bombing and other DoS attacks
The attacker can also try to perform Denial of Service on the network layer by saturating the medium with a storm of broadcast messages (message bombing), reducing nodes’ goodput and possibly impeding nodes from communicating. (This is not possible under hybrid routing protocols, where nodes cannot issue broadcast communications .) The attacker can even send invalid messages just to keep nodes busy, wasting their CPU cycles and draining their battery power. In this case the attack is not aimed at modifying the network topology in a certain fashion, but rather at generally perturbing the network functions and communications.
On the transport layer, Kuzmanovic and Knightly demonstrate the effectiveness of a low-rate DoS attack performed by sending short bursts repeated with a slow timescale frequency (shrew attack). In the case of severe network congestion, TCP operates on timescales of Retransmission Time Out (RTO). The throughput (composed of legitimate traffic as well as DoS traffic) triggers the TCP congestion control protocol, so the TCP flow enters a timeout and awaits a RTO slot before trying to send another packet. If the attack period is chosen to approximate the RTO of the TCP flow, the flow repeatedly tries to exit timeout state and fails, producing zero throughput. If the attack period is chosen to be slightly greater than the RTO, the throughput is severely reduced. This attack is effective because the sending rate of DoS traffic is too low to be detected by anti-DoS countermeasures.
Another DoS performed on the transport layer is the subtle jellyfish attack by Aad et al. , that deserves particular attention. Its authors point out that, remarkably, it does not disobey the rules of the routing protocol, even if we may argue that, strictly speaking, this is not always the case. But is indeed true that the jellyfish attack is difficult to distinguish from congestion and packet losses that occur naturally in a network, and therefore is hard and resource-consuming to detect.
This DoS attack can be carried out by employing several mechanisms. One of the mechanisms of the jellyfish attack consists in a node delivering all received packets, but in scrambled order instead of the canonical FIFO order. Duplicate ACKs derive from this malicious behavior, which produces zero goodput although all sent packets are received. This attack cannot be successfully opposed by the actual TCP packet reordering techniques, because such techniques are effective on sporadic and non-systematic reordering.
The second mechanism is the same as that used in the shrew attack, and involves performing a selective blackhole attack by dropping all packets for a very short duration at every RTO. The flow enters timeout at the first packet loss caused by the jellyfish attack, then periodically re-enters the timeout state at every elapsed RTO.
The third mechanism consists in holding a received packet for a random time before processing it, increasing delay variance. This causes TCP traffic to be sent in bursts, therefore increasing the odds of collisions and losses; it increases the RTO value excessively; and it causes an incorrect estimation of the available bandwidth in congestion control protocols based on packet delays.
DoS attacks can also be carried over on the physical layer (e.g. jamming or radio interference); in this case, they can be dealt with by using physical techniques e.g. spread spectrum modulation.
In sum, Denial of Service can be accomplished over different layers and in several ways, and is quite difficult to counteract, even on a wired medium. The topics regarding a full protection against DoS attacks are beyond the scope of this thesis, and therefore are not discussed in detail.