Ad hoc wireless networks are included portable nodes that trade packets by sharing a typical communicate radio channel. Because of the constraints of this channel, the data transmission to be shared among the nodes is constrained.
In this manner, the point in these networks is to have the option to use the transmission capacity effectively, and ensure decency to all nodes. As we probably am aware, wireless networks contrast gigantically from wired networks moreover, ad hoc wireless networks have significantly progressively explicit attributes, for example, node versatility, power requirements.
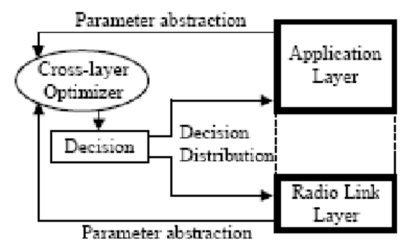
Thus, new protocols are required for controlling access to the physical medium. The special properties of the ad hoc network make the structure of a medium access control (MAC) protocol all the more testing.
Responsibilities of MAC Protocol :
· Network overhead should be low.
· Efficiently allocate the bandwidth.
· Distributed MAC operation.
· Power control mechanism should be present.
· Maximum utilization of channel.
· Hidden and Exposed problem should be removed.
· Nodes should be sync with time.
Design issues of MAC Protocol :
· Bandwidth Efficiency –
The shortage of data transfer capacity assets in these networks requires its proficient use. To evaluate this, we could state that
bandwidth capacity is the proportion of the bandwidth used for data transmission to the complete accessible bandwidth capacity.
· Quality of Service Support –
Quality of service support is difficult due to the mobility of the nodes. Once a node moves out of the reach the reservation in it is lost. In these networks QoS is extremely important because if it is being used in military environments the service support needed time to time.
· Synchronization –
Some instrument must be found so as to give synchronization among the nodes. Synchronization is significant for directing the bandwidth reservation.
· Hidden Terminal Problem –
When there is two nodes both are outside of each other’s range and try to communicate with same node within there range at the same time then there must be packet collision.
· Exposed Terminal Problem –
Uncovered nodes might be denied channel access pointlessly, which implies under usage of the bandwidth resources.